An Ultimately Secure Confidential Communication Method
(KIT STEGROUP)
This is an example of the ultimately secure confidential communication method using Internet Webpages.
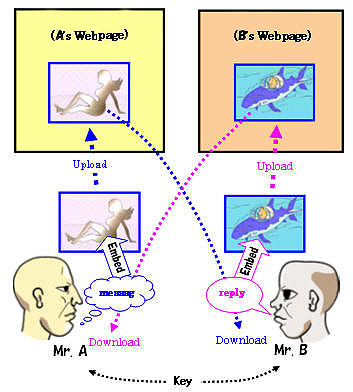
Let the two persons (Mr. A and Mr. B) in the following figure be two close friends wanting to start a secret communication. They have their respective Webpages on the Internet. Mr. A has an image data (Woman picture), and Mr. B has another image data (Killer-Whale illustration). They already agreed to use a certain common key to embed/extract messages.
This communication proceeds as,
1) A will first create a text message ("message"), and embed it in the Woman picture to produce a stego Woman picture.
2) Then A upload that picture on his Webpage.
3) Soon, B will notice it, and download the the Woman picture.
4) B extracts the hidden message by using extraction program with the key, and read the secret message from A.
5) B create a reply message ("reply").
6) B replies A in the same manner using the Killer-Whale image.
7) A receives B's reply without being known by any third party.

A Webpage-based confidential communication
The most important point in this method is that no one can detect their secret communication because they use ordinary WebPages which are open to the public on the Internet.
This communication method is available for any steganography programs including Qtech-HV v011. (However, this program has an expiration date on its embedding part.)
(Updated: June. 8, 2011. by Eiji Kawaguchi)